Cheng Lim, Bryony Evans and Clea Denham talk about the real and present danger of cyber attacks. They’re unthinkable, but the risks should be top of mind for companies and directors. They share their top tips to plan for cyber resilience.
Australia’s corporate regulator has made it clear: if a company isn’t prepared for a cyber attack, it – and its directors – risk court action.
We’ve talked a lot about cyber resilience – and planning for cyber resilience. At our upcoming Digital Future Summit, we’ll hear from Australia’s Minister for Home Affairs and Cyber Security Clare O’Neil and will talk more about cyber security and cyber resilience with Cyber Security Cooperative Research Centre CEO Rachel Falk and CyberCX Chief Strategy Officer Alastair MacGibbon. You can register for our Summit here.
But in the meantime, what does it mean to prepare for a cyber attack? What is cyber resilience? And what can happen if you don’t have it?
The implications are potentially devastating, with impacts on business operations, stolen data, regulatory investigations and potentially, class actions. Ensuring cyber resilience is critical to being able to mitigate the risks of a successful cyber attack impacting a business.
In this post, we share our insights on the ‘planning’ stage: how can you plan for a cyber attack? For cyber resilience? After all, it is a question of ‘when’, not ‘if’, you come under attack.
Cyber resilience is your ability to recover from a cyber attack and continue carry on business without material adverse impact. Planning for cyber resilience, then, is practicing how you would manage your response to a cyber attack, having the right resources in place to manage the response and most importantly, ensuring that your business is able to continue to operate without material adverse impact despite the attack.
You should therefore have your forensic investigation team and lawyers on standby, made sure that your insurance coverage will respond, have adequate IT operations resources available to deal with system shut downs, password resets, manual/alternative workarounds for key processes, and of course, making sure that you have up to date offline backups of your data that are secure. Read on.
Cyber resilience is your ability to recover from a cyber attack and continue carry on business without material adverse impact.
Planning for cyber resilience, then, is practicing how you would manage your response to a cyber attack, having the right resources in place to manage the response and most importantly, ensuring that your business is able to continue to operate without material adverse impact despite the attack. You should therefore have your forensic investigation team and lawyers on standby, made sure that your insurance coverage will respond, have adequate IT operations resources available to deal with system shut downs, password resets, manual/alternative workarounds for key processes, and of course, making sure that you have up to date offline backups of your data that are secure. Read on.
How to plan for cyber resilience?
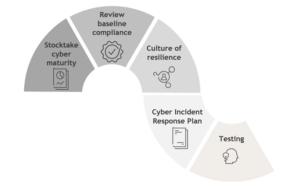
a) Stocktake on cyber maturity & benchmarking
As a first step, a company should understand its cyber maturity and benchmark itself against minimum, best practice cybersecurity standards.
It is good practice to undertake a cyber maturity review against the following generally accepted standards to evaluate and improve a company’s cyber posture:
This is often done with the assistance of cyber experts who can provide a set of recommendations to improve a company’s cyber posture following the review. If you are responsible for a critical infrastructure asset under the Security of Critical Infrastructure Act 2018, you may also be required to have and implement a Critical Infrastructure Risk Management Plan which should cover these requirements.
b) Reviewing baseline compliance
The Essential Eight is a baseline series of mitigation strategies developed by the Australian Cyber Security Centre designed to protect organisations against cyber threats. Compliance with the Essential Eight is generally seen by government and regulators as a positive sign of cyber maturity. Reviewing a company’s compliance against with the Essential Eight will also assist in assessing its cyber maturity strategy. This can be done in conjunction with or as part of the cyber maturity review referred to above, and a risk assessment undertaken to determine which maturity level a company should seek to achieve and by when.
Boards do need to understand that the Essential Eight was primarily designed to protected Microsoft Windows-based internet connected networks and that if their companies’ environments comprise significant elements of cloud services and enterprise mobility, there may be alternative mitigation strategies which are more suited to threats in those environments.
c) Promoting and developing a culture of cyber resilience
Promoting and developing a culture of cyber resilience is a key ‘soft defence’ to cyber threats. Companies should ensure regular cyber awareness training is conducted so employees are vigilant to common cyber threats, such as phishing attacks.
It’s also important that key employees are aware of any responsibilities they may have in the event of a cyber attack.
d) Preparing a cyber incident response plan
Having a cyber incident response plan is crucial for all businesses in Australia as this means that there will be a structured, considered and cohesive plan to responding to a cyber attack. KWM’s Cyber Response Guide sets out general procedures that may be in a cyber incident response plan that a company should follow in the event of a cyber attack.
e) Testing
Testing is critical to test a company’s preparedness in the event of a cyber attack. This will give a company a better level of assurance of its cyber resilience, including whether its cyber incident response plan, its business continuity plans and other controls are sufficiently robust.
Thorough testing gives assurance that weaknesses in processes or systems, including decision making, are identified before an actual event occurs.
It can especially be useful to engage in a simulated attack to ensure that management and board ‘practice’ how they would respond if there was a cyber attack.
Australia’s cyber regulatory landscape – directors take note
The increasing regularity and sophistication of cyber threats tells us cyber security and cyber resilience should be a priority of all Australian companies. This is especially important with the heightened focus of Government and Australian regulators on protecting Australia and the public from cyber threats and attacks.
The Australian Securities and Investments Commission has made it clear that it will pursue companies – and company directors – if they fail to properly discharge their duties to manage cyber risks.
“For all boards, cyber resilience has got to be a top priority. If things go wrong, ASIC will be looking for the right case where company directors and boards failed to take reasonable steps, or make reasonable investments proportionate to the risks that their business poses.” ASIC chairman Joe Longo, quoted in The Australian Financial Review
More broadly, a cyber attack may give rise to a number of key compliance and other risks for companies including:
- The obligation under the Privacy Act to take reasonable steps to protect personal information from unauthorised access or disclosure.
- Specific cyber security obligations that apply to critical assets or systems of national significance under the Security of Critical Infrastructure Act (or equivalent obligations in particular sector specific regulatory instruments, such as telecommunications, ports and airports).
- Sector or industry specific obligations that include cyber security, particularly APRA’s CPS 234 and CPS 230 prudential standards.
- Reporting and notification obligations attaching to data breaches and cyber security incidents under the above legislation and regulatory instruments.
- The decision to pay, or not pay, a ransom, and how to manage sanctions and other criminal offences in doing so.
- The obligations on a listed company to disclose the attack to the market under its continuous disclosure obligations.
- Risk of representative claims under the Privacy Act or class actions (including securities class actions for listed companies).
You will need to bring careful judgement to how you navigate this complex maze of obligations. We can bring our experience and insight to assist you in making these judgements.
Regulatory change is just around the corner
The Federal Government is expected to announce its 2023-2030 Australian Cyber Security Strategy in late 2023 – exploring a range of policy options, regulatory changes and, importantly, outlining steps that the Government will take to implement its vision of making Australia the world’s most cyber secure nation by 2030. We all will have our part to play and to comply with new obligations if this vision is to be implemented!
Want to know more? We’ll write more about cyber resilience and – critically – data governance, soon. Please reach out to KWM’s Cyber security and data breach team for advice on preparing for cyber and data incidents.
Other articles:
Managing cyber risk and incidents
Australia’s cyber landscape – how do we compare?
International comparison of cyber security regulatory settings








