Stolen data. A ransom demanded. People affected across borders. What should an organisation do when the unthinkable happens: a cyber breach? How is it managed as the drama unfolds? What could it have done beforehand to minimise risks and potential damage?
King & Wood Mallesons partners Cheng Lim, Su Chang, Nicola Charlston and Amanda Lees came together to discuss a hypothetical – yet very real – cybersecurity breach as part of the Sprint to the Finish series. Responding to the scenario in ‘virtual’ real time, they looked at responses and implications across Australia, China and Southeast Asia.
You can watch their discussion in full here. In this post, we share their key takeaways on dealing with the ever-present threat posed by cybersecurity breaches. This complexity is further heightened when it involves navigating the intricate legal and regulatory landscapes across diverse jurisdictions.
In today’s digital age, the threat of cyber breaches looms large over corporations worldwide. With the increasing interconnectedness of businesses across borders, the fallout can be complex and far-reaching. The need for effective management – not only in managing a breach, but in preparing ahead and minimising risks – is more critical than ever.
To find out more about the rapidly evolving cyber security space, visit our website.
The case study – and the immediate action
Our fictional ASX-listed company, OneMed Healthcare, owns private hospitals in Australia, China and Southeast Asia. After discovering anomalous behaviour on an Internet-facing server used for remote access, OneMed immediately activated its retainer with its incident response provider. On the investigation, it was discovered that the server had been compromised by an unknown person. Globally, approximately 1.5 terabytes of data were exfiltrated from major systems.
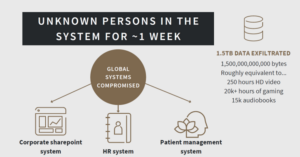
- Timely disclosure to the market: a key initial step for a listed company
“The key question is: when does the company become aware of this price sensitive information? The legal obligation is to disclose enough information to ensure that the market can assess the impact and it is not misleading – including by omission. But beyond that test there is a spectrum of acceptable disclosure details which often depends on the communications philosophy of a company.” – Nicola Charlston
For listed companies, understanding continuous disclosure obligations is paramount. In Australia, listed entities have a legal obligation to immediately disclose any information that could materially impact their share price. However, the timing of disclosure hinges on the company’s awareness and assessment of the incident’s market sensitivity.
Once a company becomes aware of any information that a reasonable person would expect to have a material effect on the price or value of that of that company’s shares, there’s an obligation to immediately tell ASX that information unless an exception applies.
Tips
- Need to have sufficient information to assess market sensitivity before disclosure.
- Craft disclosures carefully to avoid misleading investors and regulators, including by omission.
- Trading halts can be useful when a company lacks sufficient information to make a meaningful disclosure. However, companies cannot use them to delay disclosure indefinitely or avoid disclosure responsibilities.
- Who else needs notice? Consistent stakeholder communication and regulatory notifications
“In Australia, there’s currently no legal obligation to notify your employees of a breach of employee data. But as a matter of practice, everyone does. At the same time, you need to start thinking about how you notify your key stakeholders including government, regulators and customers.” – Cheng Lim
Promptly informing key stakeholders, including government agencies, regulators and affected parties, is important to maintain transparency and mitigate reputational risks. A comprehensive stakeholder management plan is essential.
The complexity of the response escalates in a multi-jurisdictional breach due to differing data protection and breach notification laws across various countries. For instance:
In Australia, the Office of the Australian Information Commissioner (OAIC) must be notified of any data breach likely to cause serious harm.
In Southeast Asia, requirements differ by country. In the Philippines, the National Privacy Commission needs to be notified. By contrast in Malaysia there is currently no requirement to notify anyone (though this is likely to change).
In China, the obligation to notify regulators is contingent on the breach’s specific circumstances, necessitating a case-by-case analysis. Regular drills and a workable plan are essential in China to effectively address cyber breach scenarios. Informal communication with authorities about the incident is also recommended due to the sensitivity of the data involved.
Customer care is paramount and businesses should offer support to affected customers to help manage the incident’s fallout. In Australia, organisations frequently contact ID Care to provide support for this purpose.
Tips
- Establish a comprehensive stakeholder management plan.
- Use one ‘single source of truth’ as a base document for all communication – for an ASX-listed company, use the stock exchange notification.
- Identify the nature of the compromised information via a forensic cyber investigation.
- Notify relevant stakeholders – starting with regulators – promptly and consistently.
- Prioritise timely notifications to affected individuals – including steps they can take to protect themselves.
- Strategise how to notify customers – via direct mail, email or other methods? – and provide customer care.
- Consider the potential impact on the organisation’s reputation.
- Multi-jurisdictional coordination and considerations
“Different jurisdictions have different notification requirements. Tailor responses accordingly.” – Su Chang
Cyber incidents require tailored responses across different jurisdictions due to varying regulatory landscapes. Engaging local counsel and adhering to jurisdiction-specific notification requirements are paramount to compliance and effective crisis management.
There are varying requirements and timeframes for data breach notification across different jurisdictions. For instance, in Australia, notifications are required to key stakeholders such as the ASX, Australian Cyber Security Centre (ACSC), Cyber and Infrastructure Security Centre (CISC) and the Office of the Australian Information Commissioner (OAIC).
In China, the local authority – in this example Shenzhen City – must be notified immediately after there is knowledge of an incident. Relevant Chinese authorities will require detailed reports.
In the Philippines, the National Privacy Commission and affected data subjects must be informed within 72 hours.
Tips
- Understand reporting requirements in each jurisdiction. Have a playbook that sets this all out.
- Follow strict reporting timelines set by local regulations.
- Coordinate with local counsel and regulatory authorities.
- Consistently communicate with key stakeholders such as employees, customers and business partners across all jurisdictions.
- Ransom payment dilemma: to pay or not to pay?
“The decision to pay a ransom is complex and depends on the specifics of the incidents. You need to come to a view as to what is the best interests of the organisation.” – Cheng Lim
In Australia, while it is not illegal to pay a ransom, there are checks to go through, particularly in relation to legislation around sanctions and instruments of crime. The government has issued a consultation paper suggesting the introduction of ransomware payment reporting requiring notification of a ransom demand and then a separate notification if a ransom is paid.
Looking across Southeast Asia… in the Philippines there’s no specific prohibition against paying a ransom, but an organization would need to carefully consider if the payment would be financing terrorism, or aiding or abetting the commission of a cybercrime or a money laundering offence.
In Malaysia it’s a similar analysis, with an additional consideration because the Penal Code requires reporting to the police if you know someone intends to commit a crime in Malaysia and a ransomware incident is a criminal offence under the Computer Crimes Act.
Many crypto exchanges are based in Singapore, which has strict rules around reporting of crimes and potential crimes, so it may need to be reported if the ransom is being paid to an exchange in Singapore.
In China the analysis is similar. There is no PRC law prohibiting the payment of a ransom in this scenario, but it’s likely that the regulator would request a report on how the issue was solved.
Tip
- Consider establishing a ransoms decision making framework in the context of the organisation’s policies, culture and risk appetite.
- The assessment of and response to ransom demands should form part of the cyber breach management plan.
- Updating the market about the cyber breach is necessary, but consider carefully the need to disclose ransom demands.
- Novel developments – the use of injunctions against cybercriminals
“The use of injunctions against persons unknown can be an effective tool to stop the dissemination of stolen information. I think we’ll see it being used more.” – Amanda Lees
Courts have shown a willingness to grant injunctions to stop bad actors, even if they can’t be identified by name. In the case of stolen data, injunctions can stop further dissemination through orders against publication by newspapers and online platforms. Given the breach of confidence – information was stolen and they’re threatening to misuse it – courts are willing to grant injunctions. Injunctions have also been obtained to stop bad actors getting the ransom paid.
Provided an organisation can identify a class of persons and describe them specifically enough, a court can issue an injunction against these persons unknown.
Courts in England, Australia, Singapore, Malaysia and other jurisdictions have granted injunctions against persons unknown. Other jurisdictions such as Hong Kong have granted injunctions against specific persons in relation to cryptocurrency and data.
Tips
- Consider different approaches that might bring benefits – such as injunctions to stop the publication of the stolen information.
- This is a potential option even if the name of the hacker is not known.
- You need to define the class of persons specifically by reference to what they’ve done – for example, “persons who have hacked the system on X days and taken data from X system, belonging to X company”.
- The order is then served on the hacker using the same means they’ve used to communicate with the victim organisation.
- Consider getting orders against third parties who are in possession of the data or likely to access the data, to stop those websites from publishing or transmitting the data.
Final word? Preparation, preparation, preparation
“It’s very important to have a workable plan to address scenarios and conduct regular drills to ensure the plan’s effectiveness.” – Su Chang
Regulators tend to focus not only on the consequence of the incident but also what led to the incident and what protection and prevention measures were in place.
Tips
- Establish a crisis management team.
- Engage with an incident response provider.
- Understand risks and prioritise them according to likelihood and severity.
- Establish a cyber breach management plan.
- Identify triggers that will set the plan into action.
- Conduct regular drills.
In the face of a cybersecurity crisis, preparation and swift action are key. Navigating a cybersecurity incident demands a proactive and coordinated approach, especially in a multi-jurisdictional setting. By understanding disclosure obligations, leveraging trading halts judiciously, prioritizing stakeholder communication, and adapting to diverse regulatory frameworks, corporations can mitigate the impact of cyber threats and safeguard their operations and reputation.
Related Content
- Unpacking Australia’s cyber security strategy
- International comparison of cyber security regulatory settings
- Cyber security guide: China
- Lessons for organisations and boards in the wake of ASIC’s Cyber Pulse Survey
- Explore more related content via the On Demand platform.







