Picture the scene – you’ve had a cyber breach, and your IT team have just told you the breach was actually an attack by a threat actor. Even worse, it is ransomware. This article by Yasmin Milligan and Mia Judkins highlights how you can prepare your business for a ransomware attack.
In the event of emergency remember – Don’t panic. You’ve read the KWM OGC Pulse article remember? You prepared and you’ve got this.
“Data is the new oil.” Ginni Rometty, Former CEO of IBM
Ransomware attacks have recently flooded the headlines and have emerged as a formidable threat to businesses across the globe. As General Counsel, you may find yourself a crucial player in your business’s response team.
Paying a ransom should always be a businesses last resort when all other controls – training, security software – have failed.
For more information about dealing with data breaches generally – see our article here.
What is ransomware?
Ransomware is a type of malicious software that encrypts a victim’s files making them inaccessible until a business pays the ransom. The ransom is usually demanded in untraceable cryptocurrencies like Bitcoin in exchange for a decryption key or to prevent the public exposure, or sale, of the stolen data. The stolen data might include commercially sensitive information, personal information, or in the cases of lawyers, privileged information. Remember our article – here – when we said that once privilege is lost in a data breach, it’s gone.
The Australia Cyber Security Centre (ACSC) advises that a business should never pay a ransom as there is no guarantee you will get your data back or that it won’t be sold or leaked online. Further, once you pay a ransom you could be subjected to further attacks because they know you’ll pay. [1]
To Pay or Not to Pay?
While the ACSC advises against it, a business may ultimately decide to pay a ransom. It’s important that you, as General Counsel, understand the legal implications of doing that. In Australia, paying a ransom isn’t generally illegal but there are a few factors to consider which may expose your business to legal risk.
Crimes – Sanctions, Anti-Money Laundering & Crimes Act
Who exactly are you paying and where are they located? That’s the big question and the answer might land you in hot water. Under Australian law, providing funds to a country with sanctions or to a terrorist organisation can lead to severe penalties. A business in Australia cannot deal with a country subject to financial sanctions.[2]
Further, the ransom payment could be seen as dealing with property intended for criminal use which could constitute anti-money laundering or proceeds of crime charges. The Criminal Code Act 1995 (Cth) prohibits dealing with money that is an instrument of crime. Paying a ransom is arguably an intentional act of doing just that. The defence of duress may be available where a claim can be made that the payment was made because there was a reasonable belief that there would be threat of harm. However, this defence may not be sound if you have alternatives like back ups or your data is encrypted.
Professional Obligations
As General Counsel you would be used to the balancing act. Dealing with a ransom request is no different. The Australian Solicitor’s Conduct Rules emphasise the importance of maintaining client confidentiality and protecting client data. While these duties may weigh in favour of paying a ransom to protect sensitive information, they must be balanced against your overarching duty to the administration of justice which would generally weigh against financially rewarding crime. The Law Society of Queensland have said that prevention is always better than a cure. They advise that, subject to some limited exceptions, ‘it is not inconsistent with a solicitor’s paramount duty to pay cyber ransom if necessary’. [3] The QLS Ethics Centre also have an excellent guidance note on whether it is ethical for a lawyer to knowingly pay a criminal. It’s available here.
What about our cyber insurance?
You should know in advance as to whether your cyber insurance extends to ransom payments. Depending on the terms of your policy, a cyber insurer may reimburse a ransom payment fully or partially. You may also need to ask your cyber insurer for consent to pay a ransom. The key takeaway here is that you need to understand your cyber insurance policy before you are in a position where you need to consider paying a ransom.
Making the Decision
It’s time. The decision to pay a ransom should not be made lightly and is something that should be considered in advance of any incident. Be prepared and give it the consideration it deserves.
You should:
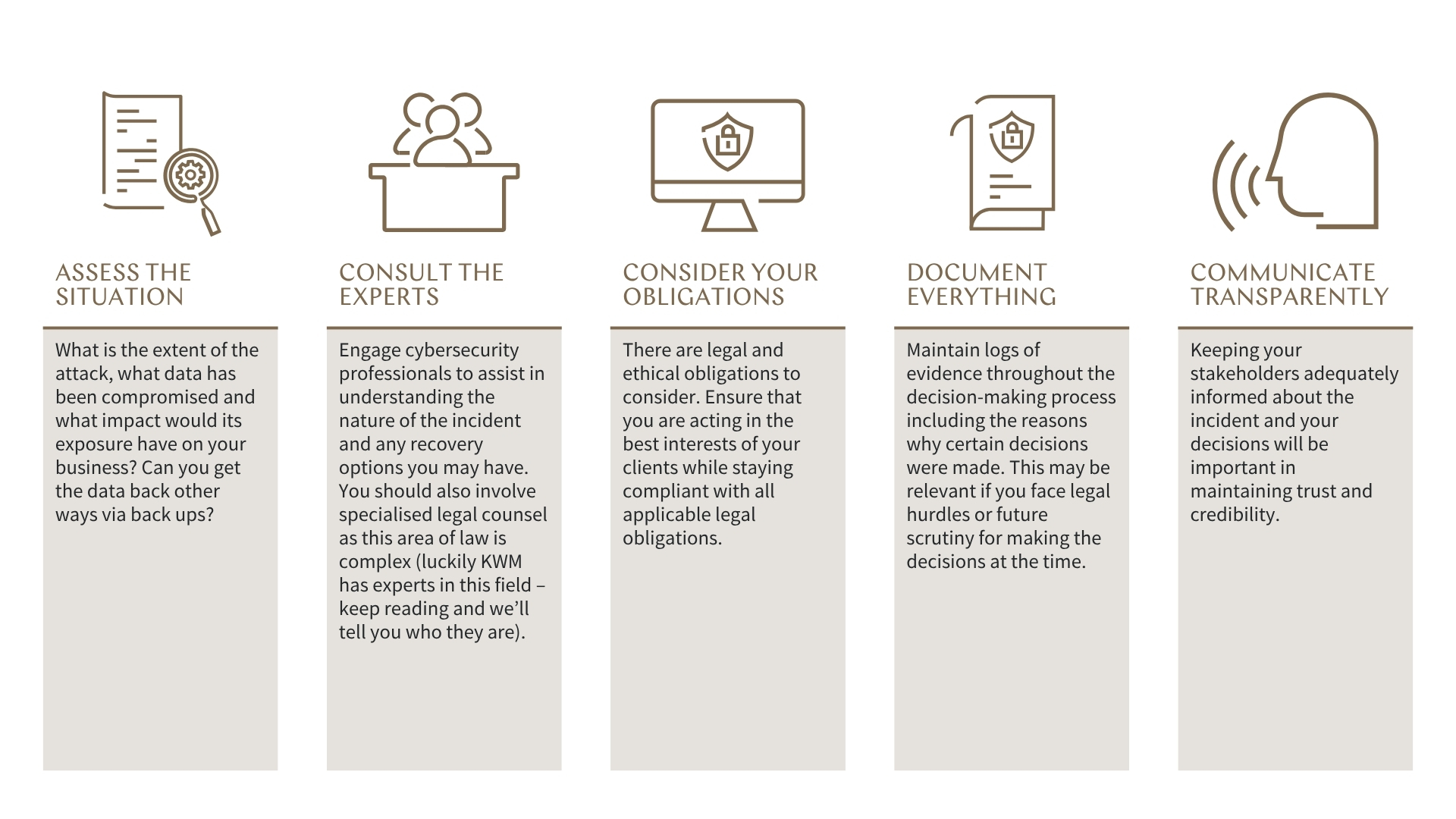
If You Pay – Reporting Obligations
The ransomware reporting obligations under the Cyber Security Act 2024 (Cth) (CSA) commenced on 30 May 2025. This means that if you are a reporting business entity (as defined in Part 3 of the CSA), you must report when a ransom or cyber extortion payment has been made or if a payment has been made on your behalf. This isn’t strictly related to cash transfers but can capture exchange of gifts, services or other benefits to the extorting entity.
A reporting business entity must report the payment online within 72 hours of making the payment or becoming aware that the payment has been made. If you make a payment and don’t report it, you could be subject to civil penalties of up to 60 penalty units (at the time of this article $19,800).
Protections from regulatory/court action
The CSA provide protections for information contained in these ransomware payment reports from regulatory or court action. Any information contained within a report is not admissible for:
- criminal proceedings (other than criminal proceedings for the provision of false or misleading information or obstruction of Commonwealth public officials);
- civil proceedings for contravention of a civil penalty provision (other than a civil penalty provision in the CSA);
- breaches of any Commonwealth, State and Territory law (including the common law) or for proceedings before a tribunal of the Commonwealth, any State or Territory.
The reporting obligation does not otherwise affect a claim of legal professional privilege in any proceedings under Commonwealth, State and Territory law (including the common law) or for proceedings before a tribunal of the Commonwealth, any State or Territory.
Protections from use or disclosure of information
The CSA also ensures that the Government cannot use or disclose any information contained in a ransomware payment report for any purpose that is not a permitted purpose. These permitted purposes include:
- Assisting the reporting business entity, and other entities acting on their behalf, to respond to, mitigate or resolve the cyber security incident.
- Performing functions or exercising powers under Part 3 or Part 6 (as it applies to Part 3) of the CSA.
- Certain proceedings under the Criminal Code (false and misleading information and documents and obstruction of Commonwealth public officials).
- Performance of the functions of a Commonwealth body or the National Cyber Security Coordinator relating to responding to, mitigating or resolving a cyber security incident.
- Informing and advising the Minister of Cyber Security, and other Ministers of the Commonwealth about the cyber security incident.
- The performance of the functions of an intelligence agency.
Conclusion
Dealing with a ransomware attack is one of the most challenging issues a General Counsel could deal with – you will play a pivotal role in navigating the legal complexities that may arise. There are a number of legal and ethical issues to consider prior to paying a ransom. Our advice in a nutshell? First – invest in cyber security – the best defence is a good offence. Second – be prepared ahead of time and know your businesses risk appetite for paying a ransom.
This article is the tip of the iceberg when it comes to ransomware and how to respond to an incident. If you ever need advice, we strongly recommend reaching out to one of our experts in our Technology space, Cheng Lim, Sector Lead, Technology, Media, Entertainment and Telecommunications Partner, Melbourne, whose contact details are here.
[2] Sanctions regimes | Australian Government Department of Foreign Affairs and Trade








