Caroline Hayward and Cecilia Askvik set out how to prepare for and manage cyber incidents and data breaches as the holiday season approaches. Kevin Tran, Head of Information Security at KWM, also provides some of his top tips to stay cyber safe this holiday. Read on for the latest in KWM’s inhouse-centred series: From our inhouse to yours.
As the holiday season is fast approaching, many are looking forward to some rest and recovery; however, threat actors do not take time off. In a previous article (Crisis Management ‘How To’: Don’t Throw Your Hands In The Air!), we advised on how to manage the variety of crises organisations can face. Cyber incidents and data breaches pose a significant threat that can easily escalate to crisis levels if poorly managed.
To avoid letting cyber grinches ruin the holiday cheer, organisations should use the lead up to the holidays to assess their cyber readiness and implement measures to handle potential cyber crises.
With an in-depth understanding of the business and the legal risks, inhouse counsel are ideally positioned to help prepare for a cyber crisis and advise on how to mitigate the risks.
Understanding the risks
Cyber criminals use the holiday season as the perfect opportunity to launch cyber-attacks, taking advantage of the fact that most employees are scrambling to finish tasks before the holidays or have already turned on their autoreplies.
Some of the most prevalent cyber threats during the holidays include ransomware and malware, phishing attacks, and DDoS attacks, but also business email compromise and online fraud. But why do attacks increase during this time of year?
Increased workload
The months leading up to the holiday season tend to be a busy period for most organisations. This leaves employees stressed and distracted, increasing the risk of human error. According to the OAIC’s latest report on notifiable data breaches, human error remains one of the leading causes of data breaches.[1]
Lack of resources
Many organisations shut down with employees taking extended leave, including the security teams. This can result in delayed detection of suspicious activity, leaving the business at greater risk of experiencing a cyber incident or data breach. The patching of systems may also be delayed, which increase the likelihood of being compromised.
Phishing scams
Phishing attempts surge during this period. Threat actors exploit this time of the year to send fake shopping deals and holiday-themed emails which lure employees into providing credentials or other sensitive information, which may allow scammers to access business devices. They may also exploit your good will and desire to help. Threat actors now leverage Generative AI to create more personalised pretexts that are more believable and harder to determine as fake.
Remote work
In the lead up to or during the holidays, many employees work remotely and use unsecured internet connection, such as via public WiFi, which can put organisations’ information at risk.
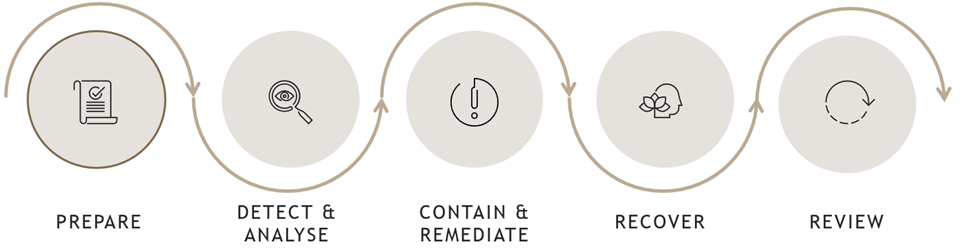
Preparation is a crucial phase in the incident response lifecycle. Some measures that will ensure your organisation is well prepared to handle potential threats include:
Preparing incident response plans
- In the event of a cyber incident or data breach, a cyber incident response or data breach response plan (‘incident response plans’) will be critical to ensure a swift and effective response. Inhouse counsel should be involved in both developing and implementing incident response plans to ensure all relevant legal and regulatory requirements are identified.
- The Australian Cyber Security Centre (ACSC) and the Office of Australian Information Commissioner (OAIC) have both issued guidance on how to prepare incident response plans. Data breach response plans can be incorporated into already existing plans, such as cyber incident response plans, ensuring a comprehensive approach to handling cyber threats.
- If incident response plans have already been prepared, a pre-holiday audit should be conducted to ensure they are up to date.
- Incident response plans must also align with the organisation’s crisis management and business continuity procedures. We explored what a Crisis Management Plan should cover in our previous Crisis Management ‘How To’ – article.
Developing a communication strategy
- Effective communication is an important component of incident response. Incident response plans should include a process for managing both internal and external communications. This should encompass template communications for different types of incidents, guidelines on when and how to notify affected individuals and other external stakeholders, and a clear division of responsibilities.
Conducting simulation exercises
- Cyber tabletop and simulation exercises should be conducted yearly to test and evaluate your organisation’s incident response and crisis management processes. These exercises are designed to:
- Simulate specific incidents and help identify deficiencies in plans and procedures
- Ensure that incident response team members know their roles and responsibilities
- Recognise opportunities for more training
- Clarify decision-making processes.
Educating employees
- Although Cyber Security Awareness Month is over, organisations should continue to prioritise cyber security awareness.
- Employees should receive regular cybersecurity training, and efforts should be made to raise awareness of potential risks and the necessary steps to take in the event of an incident. This will reduce the likelihood of human error causing a cyber incident or data breach.
We also asked Kevin to share some of his top cyber security tips to help protect your organisation.
Cyber Hygiene
- Focusing on basic cyber security controls and processes that are often low cost and provide the most impact to protecting accounts or disrupting a potential breach. These principles should be applied both at work and home.
- Multi-factor Authentication should be enabled everywhere possible, in addition to regular installation of software updates. Cyber criminals often take the path of least resistance and will prefer to breach your organisation using unpatched system vulnerabilities than invest time and money developing techniques. Many of 2023-2024’s significant data breaches were due to an unpatched vulnerability on Internet-facing systems and devices.
Managing credentials
- Switching to using dedicated credential managers that help you seamlessly create and use unique credentials everywhere. You may have a strong password, but if you use it in more than one place, once it is stolen from one site, it can be used on the others.
- Another strategy is to recommend staff to think of passwords as passphrases. A sentence that is uniquely memorable to the individual; easy to remember and hard to guess.
Cyber supply chain risk management
Even if your systems and security measures are robust, your suppliers may be the weak link being prime targets for cyber criminals during the holidays.
- Cyber criminals may compromise suppliers’ emails and use the compromised accounts to send amended bank details hoping to scam clients into sending funds to the scammers’ bank accounts. Having procedures in place to ensure employees verify the request via a trusted phone number or point of contact, rather than calling the “sender” back on a new number provided, will help keep your business secure. It is best to verify the identity of the person, using a passphrase or a fact known only between yourself and the contact.
- The same compromised supplier accounts could also be used by criminals to send malware. Organisations should establish procedures and policies that direct employees to report any suspicious attachments to the Information Security team. Like a suspicious parcel, it would not be safe to open it yourself, and you would report it. Information Security teams often have the equivalent of a bomb-disposal unit to securely open the parcel (i.e. attachment) and verify if its legitimate or detonate it in a safe location.
Mastering incident preparedness
Who should be in your incident response team?
The members of your incident response team will depend on the type and scale of the incident.
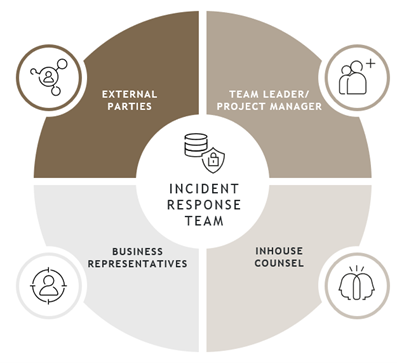
Inhouse counsel is a key member of an incident response team, with a multifaceted role that includes:
- Ensuring compliance with relevant legal and regulatory obligations, including timely notification to regulatory bodies such as the OAIC, ACSC, ASD and APRA, and as well as affected parties.
- Acting as the primary point of contact with regulators.
- Ensuring privilege is preserved.
- Reviewing communications drafted by internal and external communication teams to minimise potential reputational damage.
- Keeping a record of the response process for investigations or legal proceedings that may follow.
Business representatives from key business functions such as information security and technology, HR, Communications, C-suite executive positions and senior staff member with accountability for privacy.
External parties – depending on the type of incident, external parties that may need to be engaged include cyber experts such as extortion negotiators, cyber insurer, media experts and forensic experts.
Don’t panic!
Even with preventative measures in place, cyber incidents and data breaches cannot always be prevented. The incident response team must meet immediately to implement the incident response plan. If prior efforts have been made to develop a structured plan, this will be crucial for effectively responding to the incident.
The severity and type of incident will determine if any other plans and supporting procedures should be implemented such as crisis management plans and business continuity plans.
Communication will be key if a cyber incident or data breach occurs. The communication strategy set out in the incident response plan should be implemented promptly and consideration must be given to the type of incident and the information available at hand. In the wake of several major data breaches in Australia over the past years, many of the affected organisations have faced criticism for their poorly executed communication strategies. Poor communication will not only tarnish an organisation’s reputation but may also result in regulatory action and legal action from individuals seeking compensation.
Dedicated scribes are essential for recording key decisions, actions, the accountable persons, and the deadlines during incidents, where conversations are dynamic, and actions could easily be missed or forgotten.
For information about what the OAIC expects in terms of notifications when organisations experience a data breach and the importance of being prepared, see KWM’s article: Act on your suspicions: Key lessons from the OAIC’s latest Notifiable Data Breaches Report
Time to reflect
After the storm, the team should allocate time for a post-incident review. This review should consider if the incident could have been prevented, identify any weaknesses in the response, recommend changes to relevant incident response plans and determine if any training is necessary for the team or all employees.
Are you ready for the holidays?
Hopefully this article has shed some light on how to best prepare for a potential cyber crisis this holiday season. While threat actors are busy prepping, make sure your organisation is too!
Further information
If your business needs legal advice on crisis management and how to prepare your organisation, please reach out to your KWM contact. If your business needs specialised advice on navigating a technology crisis, please contact Cheng Lim, a Partner in our Telecommunications and Technology team.
Check out other insights from the Office of General Counsel team here and subscribe to KWM Pulse using the button below to stay across upcoming articles in areas of interest.
[1] https://www.oaic.gov.au/privacy/notifiable-data-breaches/notifiable-data-breaches-publications/notifiable-data-breaches-report-january-to-june-2024#section-spotlight-on-key-themes-and-issues









